The Security section helps ensure your AI agents operate safely, comply with regulations, and protect sensitive information through comprehensive controls and monitoring.
Security Overview
Security is a foundational aspect of responsible AI deployment, protecting both your organization and your users.
Permissions Management
Control access to agents and features
Audit Logging
Track all system activities
Compliance Dashboard
Monitor adherence to regulatory requirements
Security Scanning
Proactively identify vulnerabilities
Permissions Management
The Permissions Management section allows you to control access to agents and features:- User Permissions
- Agent Permissions
- Resource Permissions
- Temporary Access
- Role-based access control
- User-specific permissions
- Permission inheritance
- Access request workflows
Follow the principle of least privilege by granting only the minimum permissions necessary for each user and agent.
Audit Logging
The Audit Logging section tracks all system activities:
Audit logging features include:
- Comprehensive event capture
- Tamper-evident logging
- Advanced search capabilities
- Filtering and sorting
- Export functionality
- Retention policy management
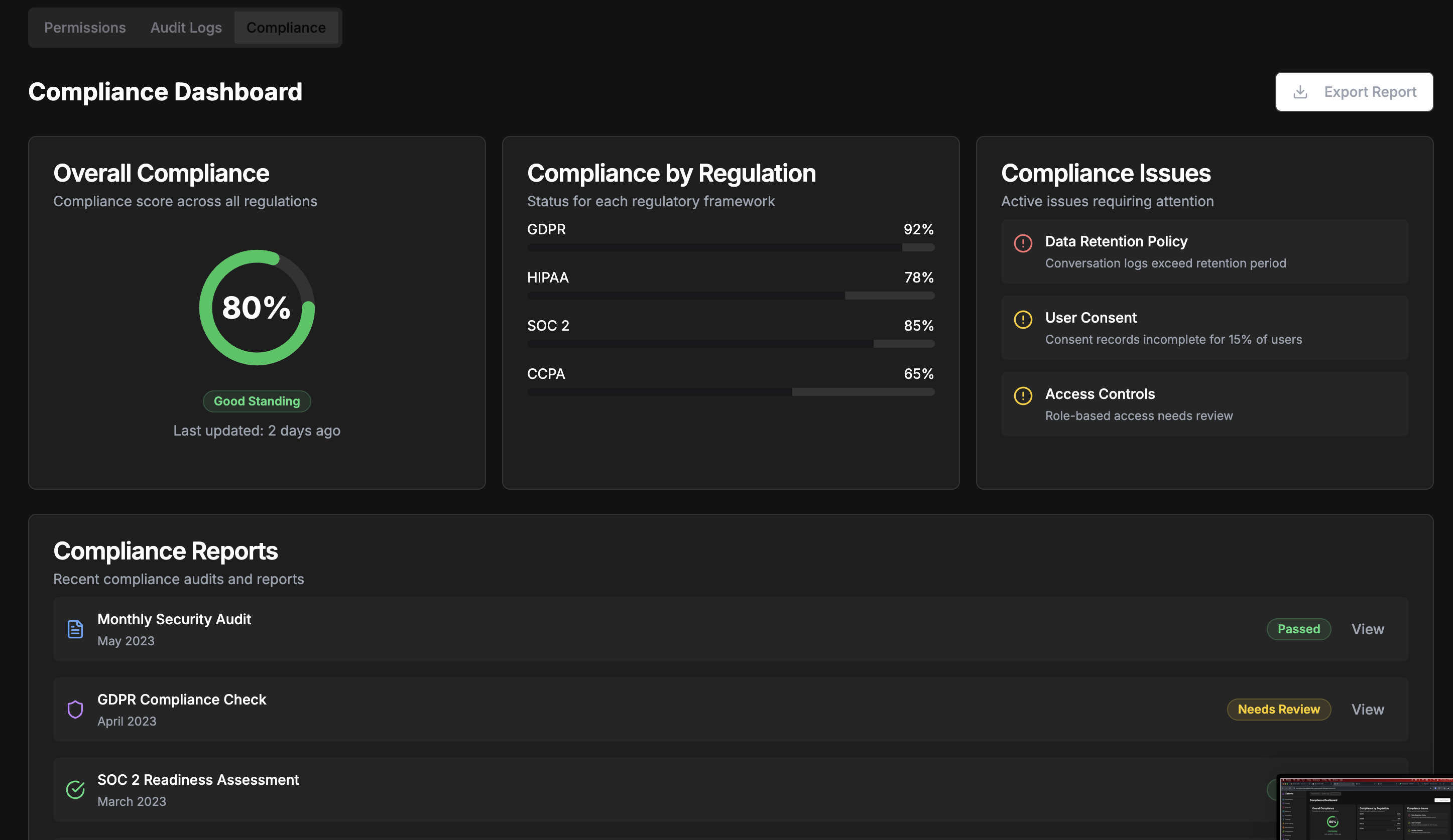
Compliance Dashboard
The Compliance Dashboard helps you monitor adherence to regulatory requirements:Compliance Status
Current compliance posture
Policy Implementation
Track policy adoption
Documentation
Manage compliance evidence
Remediation
Address compliance gaps
- Framework-specific controls
- Compliance scoring
- Gap analysis
- Evidence collection
- Audit preparation
- Regulatory updates
Security Scanning
The Security Scanning section helps you proactively identify vulnerabilities:- Prompt Injection Testing
- Data Leakage Detection
- Authentication Verification
- Rate Limiting Validation
- Detect manipulation vulnerabilities
- Test boundary enforcement
- Validate input sanitization
- Check for prompt leakage
Schedule regular security scans to identify new vulnerabilities as your agents and platform evolve.
Security Policies
Xenovia provides comprehensive security policies that can be customized for your needs:Data Protection
Safeguard sensitive information
Access Control
Manage who can access what
Content Safety
Prevent harmful outputs
Authentication
Verify user identities
Incident Response
React to security events
Compliance
Meet regulatory requirements
Security Monitoring
Xenovia provides real-time security monitoring:
Monitoring features include:
- Real-time dashboards
- Configurable alerts
- Threat intelligence integration
- Behavioral analysis
- Historical comparison
- Incident tracking